IPProof
Ipproof is a network measurement tool for performance measurements - similar to iperf or netperf. Ipproof has some unique features which make ipproof unique. This includes in-band control protocol (no additional control channel is required), delay and variation options to mimic other application protocols starting from uni-directional bulk file transfer protocol like FTP to bi-directional chatty protocols like HTTP or XMPP.
Architecture
Ipproof follows the client/server architecture. The server waits for inqueries where the client form the queries. Like netperf the server component is dump and has mainly no options! This means ipproof-server is started once and all subsequent tests/measurements are configured via ipproof-client. In contrast to iperf the commands are not transfered via a separate TCP connection to the server, rather ipproof use a in-band signaling mechanism.
Options

Destination Host
--hostname (-e) <hostname>
Payload Pattern
--payload-pattern <static | ascii-random | random | random-reduced>
Bind to Local Address
--bind (b) <address>
Differv
To set the diffserv value (DSCP) for a given flow the
--dscp option can be used. This option allow to set
the six bit of the diffserv field for IPv4 and IPv6. This
means this option accept a value of 0 to 63 (including).
--dscp val | -C val
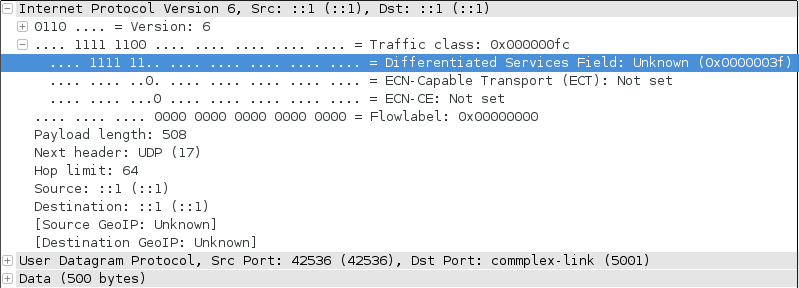
The next wireshark screenshot illustrate dscp option with value of 63 (decimal) to set all six bits.
OS Compatibility
This option is only supported under UNIX/Linux. Microsoft Windows XP do not support socket option for Diffserv setting. For Windows higher XP (i.e. Vista, 7 and up) a special libraries are available for packet QoS manipulating including setting DSCP values, called qWave (Quality Windows Audio/Video Experience).
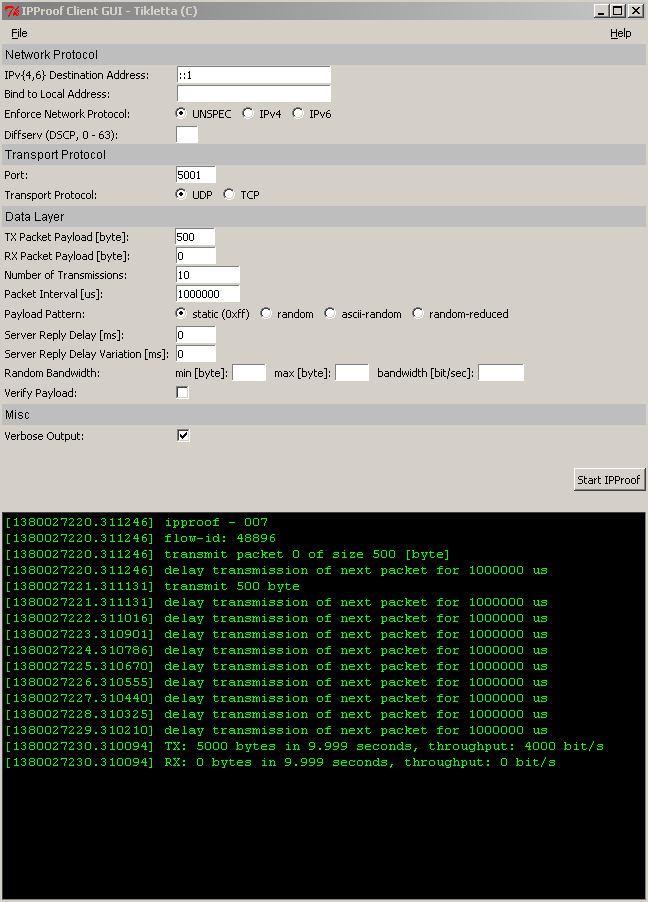
IPProof GUI
IPProof provides a cross plattform GUI using Python TK. If you have Python installed in a current or older version this GUI should work like a charm. This GUI provides no touchscreen like eye candy - it is just a wrapper around the command line interface. The following screenshot is taken from Windows XP:
Examples
UDP Data Transfer - IPv6
ipproof-server -6 -t udp
ipproof-client -6 -t udp -s 10000 -r 10 -v -v -v -e ::1
Installation
UNIX/Linux
cd ipproof/unix sudo make install
Microsoft Windows
IPProof Extensions
Parallel Measurement Environment
Scenario File Syntax
at 0.0 [ ipv4 destination:127.0.0.1 port:5001 tranport-protocol:tcp txpacketsize:1000000 rxpacketsize:10 iterations:1 ] at 0.0 [ ipv4 destination:127.0.0.1 port:5002 tranport-protocol:tcp txpacketsize:1000000 rxpacketsize:10 iterations:1 ] at 10.0 [ ipv4 destination:127.0.0.1 port:5001 tranport-protocol:udp txpacketsize:10000 rxpacketsize:10 iterations:1 ]

Analyzes
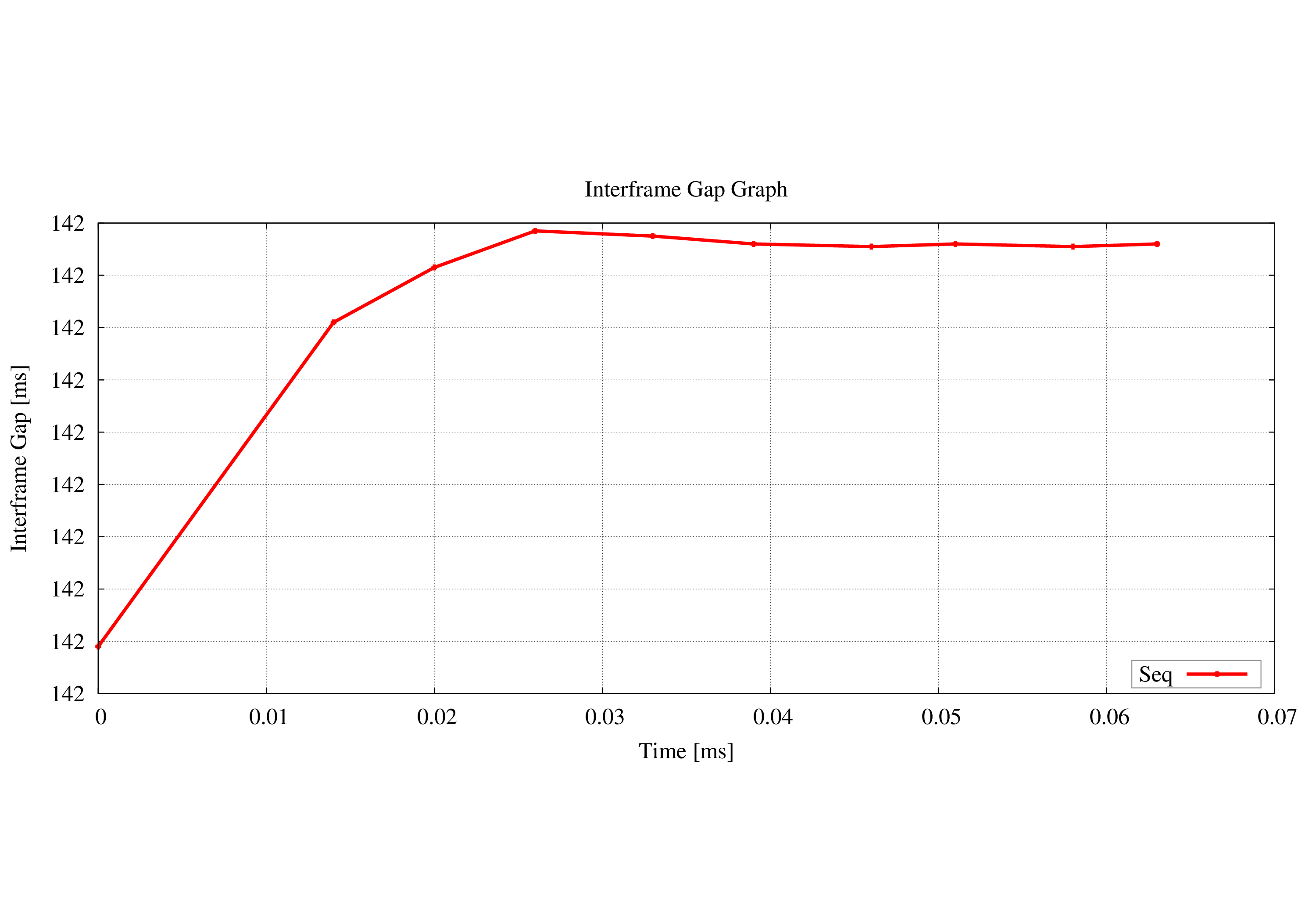
IPProof comes bounbled with an Python script to analyse packet loss and packet delay. To analyse these characteristics the script requires a PCAP file captured at sending side and one at receiver side. This setup is the bare minimum to calculate packet loss. To additionally calculate interface gap (packet delay) both peers required synchronized clocks (e.g. via GPS).
Internals
In-Band Signaling Mechanism and Header
This section describe IPProof internal behavior to extend IPProof.
Header Format
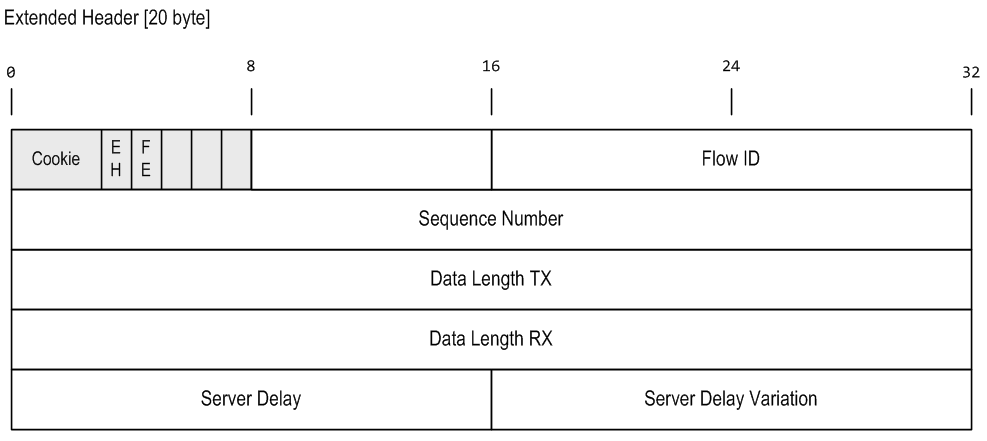
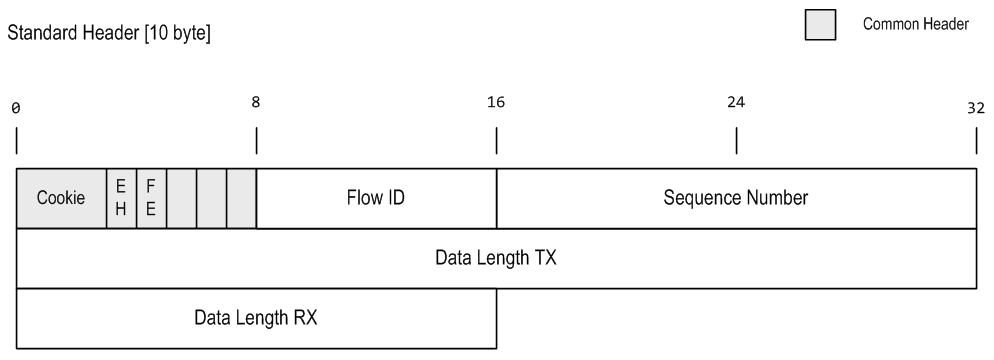
IPProof encode a small header in the very first payload bytes. Depending on the payload size a minimal or extended header is used. The minimum header limits the minimum payload size: data transfered with IPProof must be at least 10 bytes in size.
Minimal Header
Extended Header
The Extended Header is used when payload size is larger then 10 bytes.